How to self-host a Jitsi Meet server with password protection
The Jitsi Meet service can also be self-hosted. Using the open-source Jitsi Meet server, you can operate private, encrypted videoconferencing on the Internet, on a domain you control.
The following instructions show how to install the Jitsi Meet server on a VPS and configure authorization, so a username and password is required to create new meetings. These steps require an account with a VPS provider, such as Linode or Digital Ocean, and a registered domain name.
Create a Debian 9 VPS
Begin by creating a new VPS for your Jitsi Meet server. In the dashboard of your VPS provider, create a new virtual host running Debian 9, with at least 2 GB of RAM (recommended).
For example, if you are using Linode, from your Linode dashboard, choose Create > Linode. Under Choose a Distribution, select Debian 9 and a Linode plan that offers 2 GB RAM.
Or, if you are using Digital Ocean, from your Digital Ocean dashboard, choose Create > Droplets. Under Distributions, choose Debian 9.12 x64 and a Droplet plan that offers 2 GB RAM.
Update DNS records
Add A/AAAA DNS records to your domain with the subdomain name and the IPv4/IPv6 address of your new VPS.
For example, to host Jitsi at video.mydomain.com, log in to your domain registrar account, and edit the DNS records for mydomain.com. Add two records for hostname video, one with the IPv4 address (the "A" record), and one with the IPv6 address (the "AAAA" record).
If you don't want to use a subdomain (e.g., mydomain.com instead of video.mydomain.com), leave the hostname blank in the A/AAAA records.
Upgrade and secure VPS
Open a terminal or command prompt window. SSH to your VPS as the root user.
Update the package list and upgrade installed software.
Install sudo and UFW (Uncomplicated Firewall).
Configure firewall
Configure UFW to allow TCP communication on the ports used by SSH, HTTP, and HTTPS, and to allow UDP traffic on port 10000.
Enable the firewall.
Set the hostname of the server to your FQDN, for example, video.mydomain.com.
Add the FQDN to your hosts file. Open the file /etc/hosts in a text editor, such as nano.
Find the line 127.0.0.1 localhost and append your FQDN.
Save the file and exit the editor. (In nano, press Ctrl+O, Enter to save the file, and Ctrl+X to exit.)
Create a user with sudo rights
Add a new user account. Replace myuser with your desired username.
Add this user to the 'sudo' group, so it can run commands with sudo.
Disable root SSH
Open the SSH daemon configuration file in a text editor.
Find the line PermitRootLogin yes, and change yes to no.
Save the file and exit the editor (Ctrl+O, Enter, Ctrl+X in nano).
Then, restart the SSH daemon.
Add SSH key
The following steps add an SSH key to the server to provide stronger security. These steps are optional, but recommended.
If you are still logged in to your SSH session, log out.
If you do not have an existing SSH key, create one on your local machine. (If you have an existing key you want to use, skip this step.)
Press Enter to use the default public/private key file names.
When prompted, choose a strong passphrase as an additional layer of security.
Transfer the key to your server using SSH. On Linux and macOS:
On Windows 10:
Log in to the VPS using your SSH key.
When prompted, enter the key passphrase.
Next, disable password-based SSH authentication on the VPS. Open the SSH daemon configuration in a text editor.
Find the line that reads #PasswordAuthentication yes. Change yes to no, and remove the # to uncomment the line.
Save the file and exit the editor. Then, restart the SSH daemon.
SSH logins are now restricted to users with the public and private key files who know the key passphrase.
As good practice, restrict access to the .ssh directory to your user only.
Install Jitsi Meet server
The following steps install the Jitsi Meet server package on your VPS.
First, enable installation of APT packages over HTTPS.
Add Jitsi to the list of APT repositories.
Download and install the public encryption key of the Jitsi repository.
Update your APT package list.
Install the Jitsi Meet server.
When prompted for the hostname of the current installation, enter your FQDN, including the subdomain, if any.

Choose Generate a new self-signed certificate.

Next, replace the self-signed certificate with a trusted certificate provided by Let's Encrypt.
When prompted, enter an e-mail address to receive alerts or notifications about your certificate.
Certificate generation should take less than a minute. When it's done, your Jitsi Meet server is live on the Internet at your domain. You can create new meetings and invite users by sharing the meeting URL.
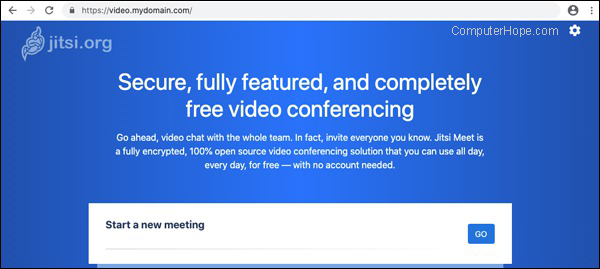
However, the application is not secure. Anyone who goes to your domain can create a new Jitsi meeting hosted on your server.
To prevent unauthorized access, the following steps enable authentication, so a username and password are required before a meeting is created.
Configure Prosody
Prosody is a component of Jitsi Meet that provides XMPP communication between users and the server. The following steps configure Prosody to authenticate users who create a Jitsi meeting.
Create a guest domain
On the VPS, switch user to root.
Change to directory /etc/prosody/conf.avail/.
Open the file fqdn.cfg.lua in a text editor.
In the VirtualHost section for your domain, change the authentication method from anonymous to internal_plain.
Above the existing VirtualHost section for your site, insert a new VirtualHost section. The name of this VirtualHost is guest.fqdn. For example, insert the following lines to create a new guest VirtualHost for the site video.mydomain.com.
Save the file and exit the editor. Then, exit the root account.
Install module storage_memory
An optional Prosody module, storage_memory, enables a temporary memory storage for persistent information, including user session data. The module source code is available from Prosody's Mercurial repository.
Install Mercurial on your VPS.
Create a temporary directory and change to it.
Clone the prosody modules repository to a new directory, prosody_modules.
Copy file mod_storage_memory.lua to directory /usr/lib/prosody/modules.
Create a Jitsi anonymous domain
Configure Jitsi Meet to use an anonymous domain for users invited to a meeting.
Open the file /etc/jitsi/meet/fqdn-config.js in a text editor.
In the config variable, in the hosts key, add a new key named anonymousdomain, with the value guest.fqdn.
For example, if your guest domain is guest.video.mydomain.com, the entry should appear as follows. Note that the line ends in a comma.
Save the file and close the text editor.
Configure Jicofo
Jicofo (Jitsi Conference Focus) is a component of Jitsi Meet that manages user sessions. The following steps configure Jicofo's SIP (Session Initiation Protocol) to use XMPP authentication.
Open the file /etc/jitsi/jicofo/sip-communicator.properties in a text editor.
Add a new line with the following configuration. Replace video.mydomain.com with your FQDN.
Save the file and exit the editor.
Create Jitsi admin users
Prosody administrative functions are accessed using the prosodyctl command ("Prosody control").
To create a user/password for Jitsi Meet, run the command prosodyctl register username fqdn password.
Repeat this command for any additional users you want to create.
Only users who create new meetings require an account. Connecting to an existing meeting does not require authorization.
Restart services
To apply the new configuration, restart the affected services.
Now, only users with the correct username/password combination can create new meetings on your Jitsi server.
Creating new meetings
Follow these steps to create new meetings on your Jitsi server.
In a browser
On a laptop or desktop computer, open a browser to the address of your Jitsi server.
Under Start a new meeting, type a name for the meeting, and click Go.
This name appears in the URL you share with invitees. Meeting names are not case-sensitive.

Click I am the host.

Enter the Jitsi username and password you created, and click OK.

If authentication is successful, the conference goes live immediately.
You only need to authenticate once per browser session. To forget your current login, clear your browser cookies, see: How do I enable, disable, view, or delete Internet cookies?
In the mobile app
Get the Jitsi app for iOS at the App Store, or for Android at the Play Store.
Open the Jitsi Meet app. Tap the menu button and choose Settings.

In settings, under Server URL, enter the domain of your Jitsi server.

Go back to the main app window. Enter a new meeting name, and tap create/join.

Tap OK.

Enter the Jitsi username and password you created, and tap OK.

If the app seems to freeze at "Connecting," wait a few seconds for authentication to complete.

